Setting up LUKS – Keeping the Data Safe – Securing a System
Setting up LUKS
- First, install the required packages with the following dnf command:
dnf -y install cryptsetup clevis clevis-luks clevis-dracut
- Now, we will encrypt the entire raw data device. By encrypting the entire device, all meta data about the volume is encrypted, along with the actual data itself. In this example, we have /dev/sdb, which is a small 20 GB device. You can see by checking all the block devices with the lsblk command:
[root@clevis ~]# lsblk
NAME MAJ:MIN RM SIZE RO TYPE MOUNTPOINT
sda 8:0 0 100G 0 disk
├─sda1 8:1 0 1G 0 part /boot
└─sda2 8:2 0 72.9G 0 part
├─ol-root 252:0 0 50G 0 lvm /
├─ol-swap 252:1 0 7.9G 0 lvm [SWAP]
├─ol-var 252:2 0 5G 0 lvm /var
├─ol-home 252:3 0 5G 0 lvm /home
└─ol-var_log 252:4 0 5G 0 lvm /var/log
sdb 8:16 0 20G 0 disk
sr0 11:0 1 1024M 0 rom
- Encrypt /dev/sdb with the following command:
cryptsetup luksFormat –type luks2 –cipher aes-xts-plain64 \
–key-size 512 –hash sha256 –use-random –force-password /dev/sdb
WARNING: Doing this will delete ALL DATA on the device, including any partitions:
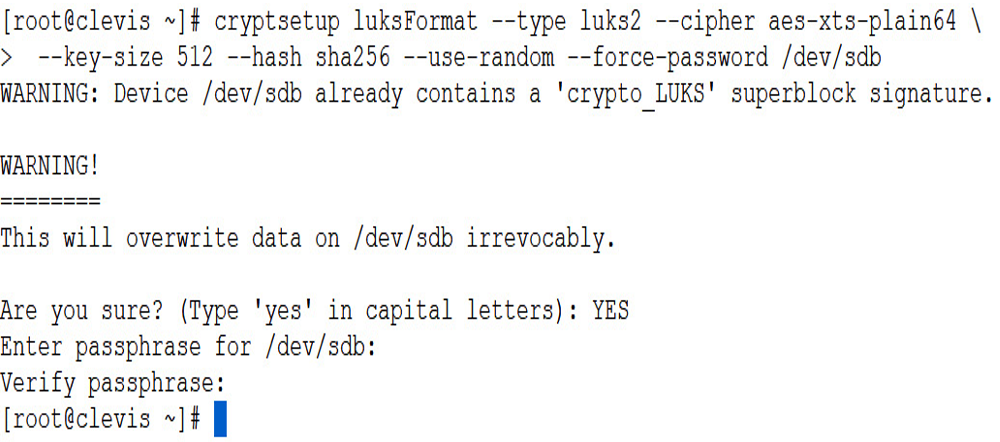
Figure 9.6 – Encrypting the drive
When running the command, you will also be prompted for a passphrase. DO NOT LOSE THIS or you will be unable to decrypt the drive manually.
- Next, let’s manually unlock the drive using the previously saved passphrase with the following command:
cryptsetup –verbose luksOpen /dev/sdb datadisk1
Once unlocked, you should see the disk in /dev/mapper:
[root@clevis ~]# ls /dev/mapper/datadisk1
/dev/mapper/datadisk1
- Now we can use /dev/mapper/datadisk1 like any normal disk. In the example, let’s create a xfs filesystem on /dev/mapper/datadisk1:
mkfs.xfs /dev/mapper/datadisk1
We will also make a mount point /data:
mkdir /data
- To use the disk, we need to pull the UUID of the disk. This is done with the following blkid command. The UUID will be used to identify the disk to decrypt it later:
[root@clevis ~]# blkid -s UUID /dev/mapper/datadisk1
/dev/mapper/datadisk1: UUID=”58c9f051-f243-4c42-af4f-62d2e3e3b90f
“
- Mounting the filesystem on reboot required us to add the fstab entry with the following command:
echo “UUID=58c9f051-f243-4c42-af4f-62d2e3e3b90f /data xfs defaults 0 0” | sudo tee -a /etc/fstab
- Now we can mount the disk with the following command:
mount /data
- Next, we need to bind a Tang key to the device using Clevis with the following command. We will pass the device and Tang server information via the following command line. You will need to use the existing LUKS password to add the keys to Tang:
[root@clevis ~]# clevis luks bind -d /dev/sdb tang ‘{“url”:”http://tang.m57.local”}’
Warning: Value 512 is outside of the allowed entropy range, adjusting it.
The advertisement contains the following signing keys:
RxdbjAY7_N19UEYBO6XIUVosv0s
Do you wish to trust these keys?
[ynYN] Y
Enter existing LUKS password:

